Introduction
Hi everyone, I’m Dylan from Money Forward ERP’s Kansai Development Department. Last month, I had the opportunity to participate in my first Capture The Flag (CTF) event at our Kansai Branch Office. In this article, I’d like to share my experience and the excitement I felt during this innovative development camp.

Why Kansai CTF Matters
Occasionally, the Kansai Branch team organizes events to help engineers connect across teams, encouraging everyone to think outside the box, which generates exceptional ideas and builds momentum throughout our organization.
This time, the CTF event focused on fostering cross-team collaboration in Kansai while cultivating a security-first culture among engineers. It provided us with a deeper understanding of security principles and practical defense strategies, all while enjoying challenging engineering problems.
The CTF world features two main formats: Attack & Defense CTF and Jeopardy (Problem-Solving) CTF. We chose the latter for this event to maximize creative potential and ensure broader participation.
My Favorite Moments!
Beyond the Ordinary: CTF’s Creative Approach
When I first heard about the security theme, I anticipated something conventional, possibly even dull. However, I was pleasantly surprised by the innovative format – unlike any development camp I’d previously experienced.
Hacking and learning! The event centered on Web Exploitation, covering critical security vulnerabilities including SQL Injection, Cross-Site Scripting (XSS), Cross-Site Request Forgery (CSRF), and Broken Authentication and Session Management.
Let me walk you through an example security challenge: Have you ever wondered how to access a website without knowing legitimate credentials?

The solution: In the password field, entering ' or 1=1 -- causes the application to execute the query: SELECT * FROM users WHERE username = '' OR 1=1-- ' AND password = 'foo'. Since the comment sequence (–) causes the system to ignore the remainder of the query, this effectively becomes: SELECT * FROM users WHERE username = ' ' OR 1=1, granting successful authentication.
Our CTF event built upon this concept in an engaging format. Each team created a “challenge” – essentially a website – and concealed their flag somewhere within it (cookies, access tokens, file system, URLs, etc.) at three different difficulty levels. Teams then attempted to “break” into other teams’ sites, extracting the correct flag values. The team accumulating the most points emerged victorious.
Additionally, each team prepared solution presentations for the Solution Sharing LT session on day two. This approach proved both informative and exhilarating – we enjoyed a full day of ethical hacking, and even when unsuccessful, we gained valuable insights during the solution sharing.
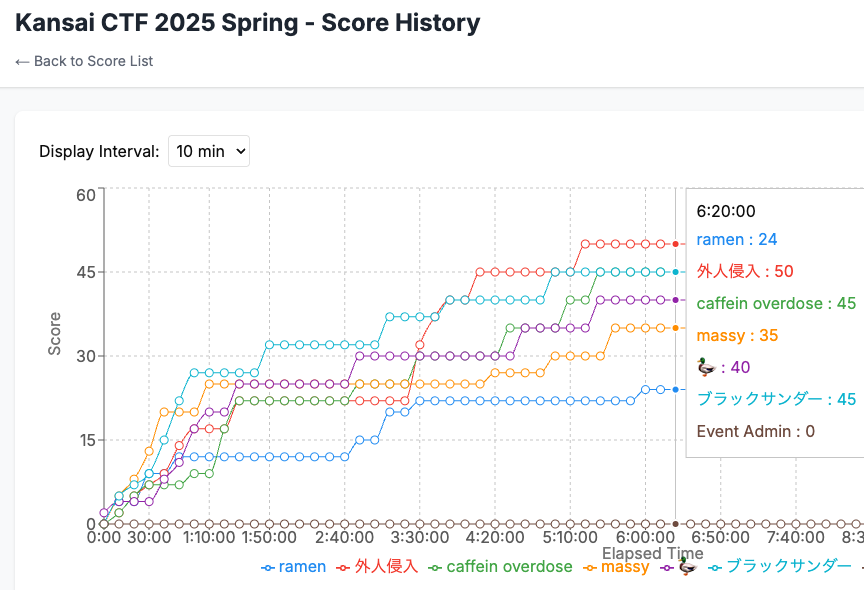
The event had a live scoreboard that kept track of each team’s points as they successfully hacked into websites and found the hidden flags. The competition was close, with teams staying very competitive throughout. In the end, team 外人侵入 (humorously named for being the only non-Japanese team) won by getting a perfect score and became the champions!
In the Hacker’s Mindset: Thrills of the Challenge
During the challenge-creation phase, I was thrilled to devise different hiding places for our team’s flags and implement multi-step processes to protect them. It felt like designing an intricate puzzle box with clever safeguards to deter intruders.
Developing these challenges required adopting a hacker’s perspective – something I’d never consciously explored before. When we switched to solving other teams’ problems, I experienced what it’s like to think like an actual penetration tester. This dual perspective significantly enhanced my understanding of security vulnerabilities and profoundly increased my awareness of potential risks.
Valuable Lessons Gained
This event brilliantly fostered a security-first mindset among engineers while ensuring everyone had FUN and created meaningful connections with colleagues we don’t typically collaborate with.
Fortifying Digital Defenses: Security Insights
I appreciated how, despite the entertaining format, we acquired substantial knowledge about security – from various attack vectors to effective defensive strategies. Some teams showcased remarkably creative security challenges that introduced concepts entirely new to me.
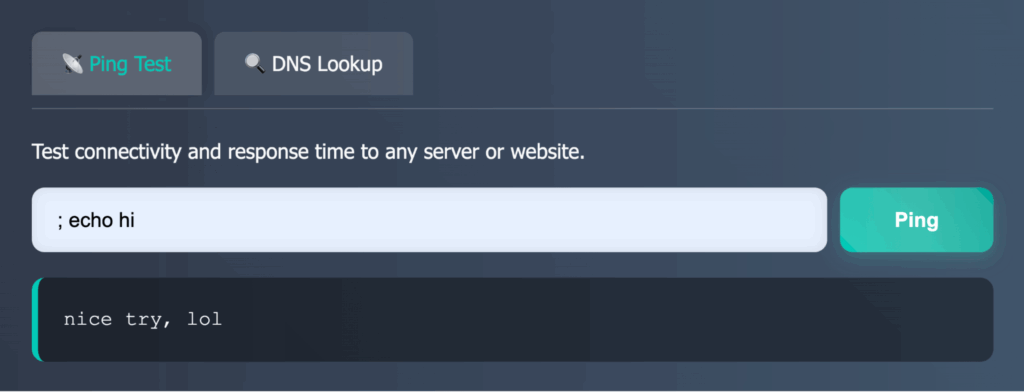
One of the most memorable challenges at the event was the clever 5-point problem designed by team ブラックサンダー (named after “Black Thunder”, a popular Japanese chocolate bar known for its crunchy cookie pieces and affordability). They created a website that allowed users to use the ping command to check server responses. The real challenge was figuring out where they had hidden the flag.
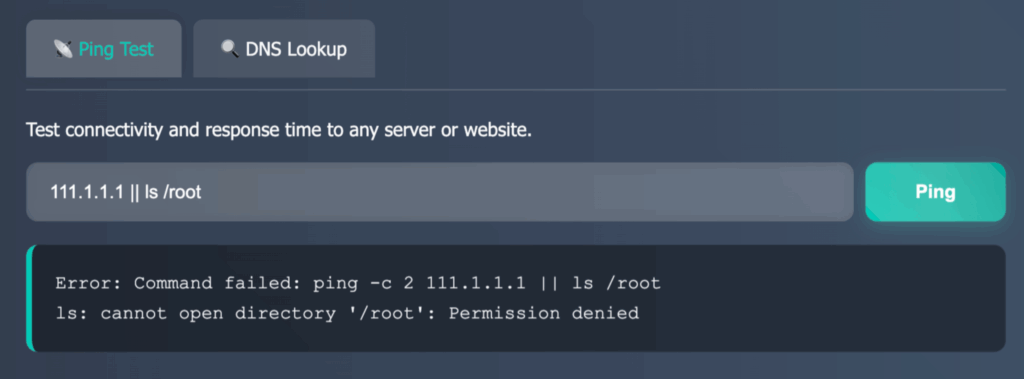
We started by trying an OS command injection with ; echo hi, but received a playful response: nice try, lol. It was clear they had anticipated this move and had defenses in place. Not giving up, we found that using the || operator could run extra commands. We tried ls /root on their server, but got a Permission denied error, showing that access was restricted. This setback didn’t stop us; it only motivated us to keep going.
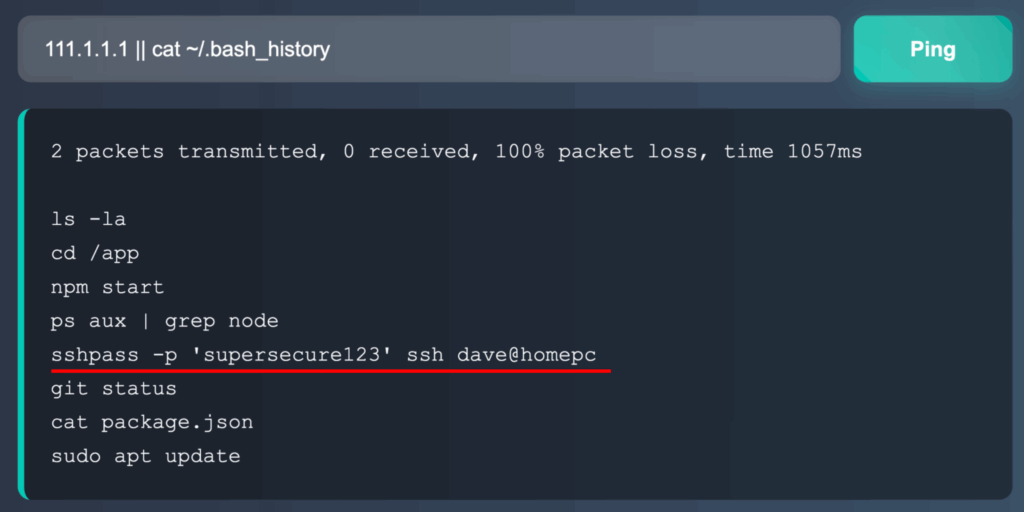
Our efforts paid off when we discovered that user passwords were accidentally exposed in the .bash_history file. By using the command 111.1.1.1 || cat ~/.bash_history, we got the password, which let us access the /root/flag.txt file on the server and get the flag.
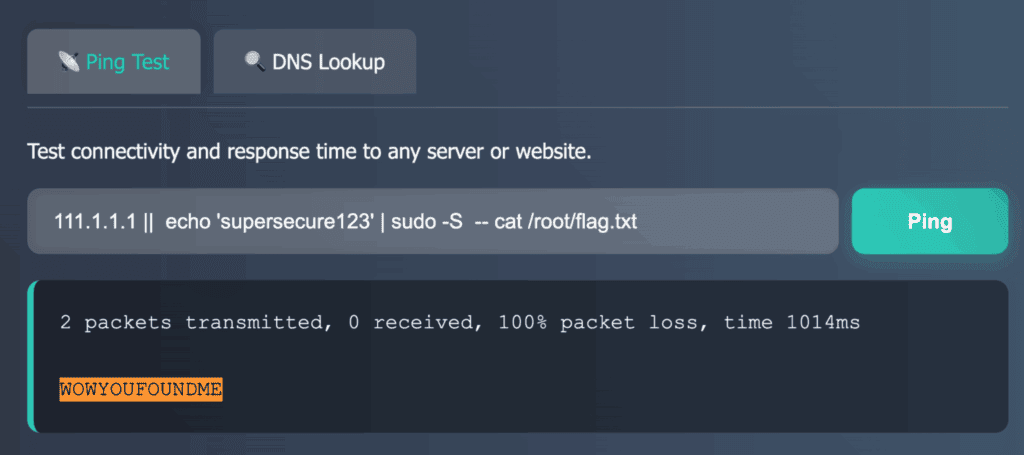
This challenge was a great example of creativity and complexity, requiring us to go through several steps and use different attack methods. It showed the innovative spirit of the event and is a great reason to join future CTFs.
The Human Element: Mastering Social Engineering
The event provided excellent opportunities to connect with colleagues outside my immediate team. It also offered Japanese team members valuable practice with English communication skills. We concluded with an awards ceremony and social gathering featuring delicious food and engaging conversation where everyone shared their impressions and genuine appreciation for their teammates.
I was impressed by how we embodied our MVVC values throughout the CTF: demonstrating Professionalism in teamwork and adhering to schedules, working with Speed when creating and solving security challenges, embracing Evolution through creative problem-solving, and showing Respect for one another during the after-party – all while having Fun!
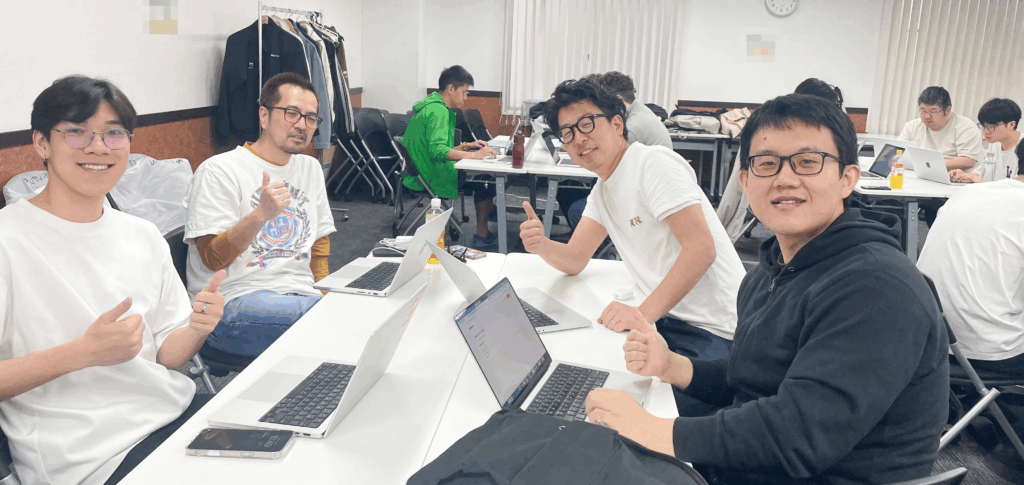

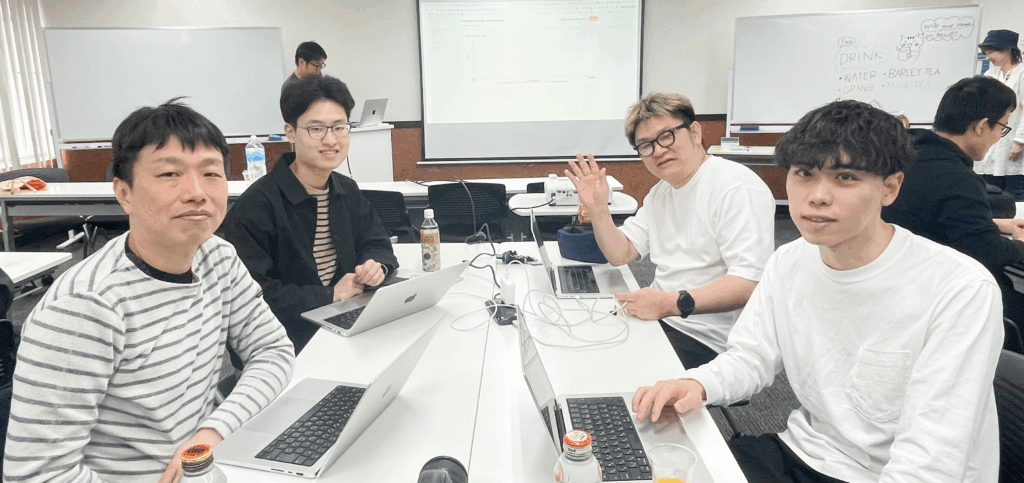

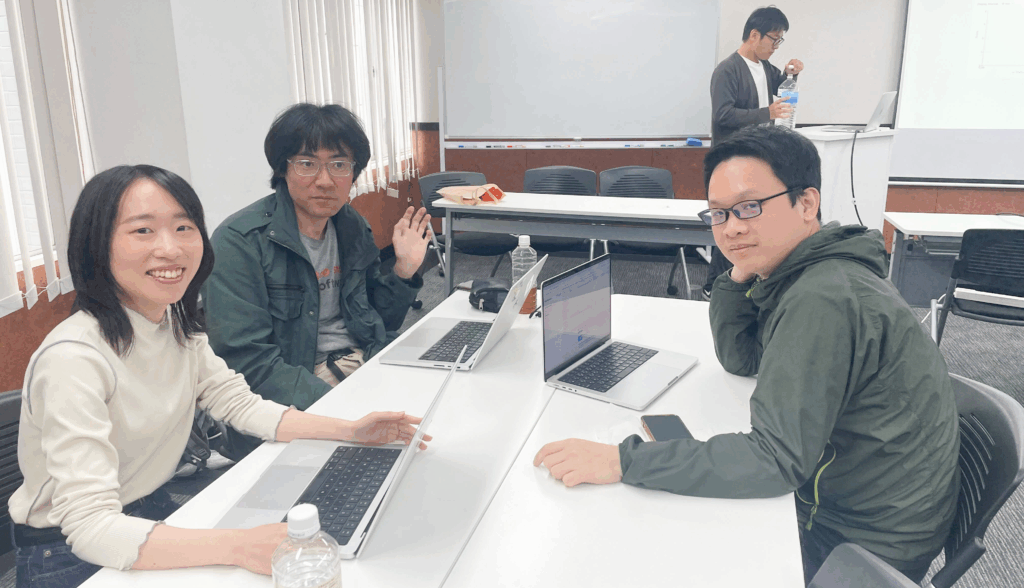

See how each team member is having fun while tackling cybersecurity challenges. This lively environment builds teamwork and showcases the thrill of a CTF event, offering both excitement and valuable learning.
Looking Forward
As I reflect on this enriching experience, I can’t help but encourage every engineer to participate in a CTF event at least once in their career. Beyond the technical skills gained, the collaborative problem-solving and security awareness you’ll develop are invaluable in today’s digital landscape.
For those who might feel intimidated by security topics, remember that I too approached this event with some hesitation. However, the supportive environment, well-structured challenges, and shared learning experience made it accessible and enjoyable for participants of all skill levels. The Kansai CTF succeeded not just as a technical exercise but as a comprehensive professional development opportunity that strengthened our team bonds while enhancing our security expertise. I’m eagerly looking forward to the next event and the new challenges it will bring.
If you’re curious about participating in future CTF events at Money Forward, feel free to reach out – I’d be happy to share more details about my experience or answer any questions you might have. Let’s continue learning, hacking, and growing together!
